|
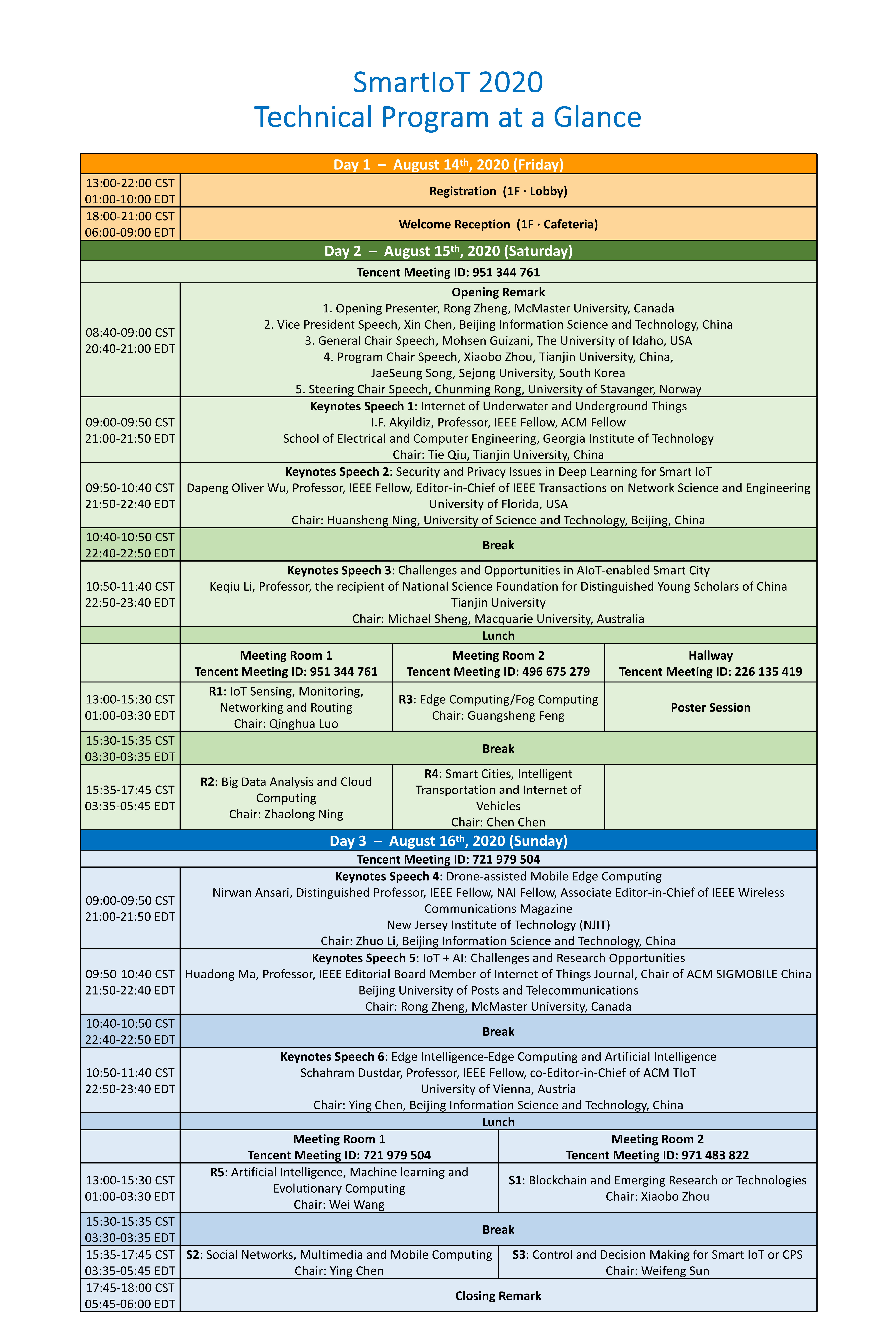
Full Program
Day 2 – August 15th, 2020 (Saturday) – Meeting Room 1 & Tencent Meeting ID: 951 344 761
Time:13:00-15:30 CST, 01:00-03:30 EDT
• Talks——R1: IoT Sensing, Monitoring, Networking and Routing
1.Performance Evaluation and Optimization for Kyber on the MULTOS IoT Trust-Anchor
Keith Mayes (University of London)
2.Quantitative Study on Impact of Node Selfishness on Performance of MANETs
Axida Shan (Xi’an University of Technology,
Baotou Teachers’ College), Xiumei Fan (Xi’an University of Technology) and Xinghui Zhang (Xi’an
University of Technology, Ankang University)
3.Analysis on the Usage of Topic Model with Background Knowledge inside Discussion Activity in Industrial Engineering Context
Muhammad Luthfi (Waseda University), Satoshi
Goto (Waseda University) and Osamu Yoshie (Waseda University)
4.NetCruiser: Localize Network Failures by Learning from Latency Data
Haoshi Ren (Tianjin University), Lihai Nie
(Tianjin University), Hongyun Gao (Tianjin University), Laiping Zhao (Tianjin University) and
Jianchao Diao (Tianjin Innovation Development Institute)
5.A Novel Diagnostic Algorithm for Heart Disease in ECG Monitoring System
Zhengyang Gu (Communication University of
China), Kehua Jiang (Communication University of China) and Qi Zhou (Suzhou Mitai Artificial
Intelligence Institute)
6.Accurate Underwater Localization Through Phase Difference
Qinghua Luo (Harbin Institute of
Technology), Chunyu (Harbin Institute of Technology), Xiaozhen Yan (Harbin Institute of
Technology), Cong Hu (Guilin University of Electronic Technology), Chuntao Wang (Shandong New
Beiyang Information Technology Co., Ltd.) and Jinfeng Ding (Shandong New Beiyang Information
Technology Co., Ltd.)
7.Dynamic Probabilistic Model Checking for Sensor Validation in Industry 4.0 Applications
Xin Xin (University of Glasgow), Sye Loong
Keoh (University of Glasgow), Michele Sevegnani (University of Glasgow) and Martin Saerbeck
(Digital Service, Centre of Excellence, TUV SUD Asia Pacific)
Time:15:30-15:35 CST, 03:30-03:35 EDT
• Break
Time:15:35-17:45 CST, 03:35-05:45 EDT
• Talks——R2: Big Data Analysis and Cloud Computing
1.New Method of MSCA for Edge Computing
De-gan Zhang (Tianjin University of
Technology), Hao-li Zhu (Tianjin University of Technology), Ting Zhang (Tianjin University of
Technology) and Jia-xu Wang (Tianjin University of Technology)
2.Energy Efficient Resource Allocation and Computation Offloading Strategy in a UAV-enabled Secure Edge-Cloud Computing System
Umar Ajaib Khan (Chongqing University of
Posts and Telecommunications), Waqas Khalid (Chongqing University of Posts and
Telecommunications) and Saifullah (Chongqing University of Posts and Telecommunications)
3.Increasing the pervasiveness of the IoT: fog computing coupled with pub&sub and security
Sabrina Sicari (University of Insubria),
Alessandra Rizzardi (University of Insubria) and Alberto Coen-Porisini (University of Insubria)
4.An access selection mechanism in 5G network slicing
Yangguang Lu (Beijing Information Science &
Technology University), Xin Chen (Beijing Information Science & Technology University), Ranran
Xi (Beijing Information Science & Technology University) and Ying Chen (Beijing Information
Science & Technology University)
5.Deep Reinforcement Learning for Pre-caching and Task Allocation in Internet of Vehicles
Teng Ma (Beijing Information Science &
Technology University), Xin Chen (Beijing Information Science & Technology University), Zhuo Ma
(Beijing Information Science & Technology University) and Ying Chen (Beijing Information Science
& Technology University)
6.Research on Computing Task Allocation Method Based on Multi-UAVs Collaboration
He Dong (Jiangsu Automation Research
Institute), Nan Wu (Harbin Engineering University), Xinying Gao (Harbin Engineering University)
and Guangsheng Feng (Harbin Engineering University)
7.Research of edge caching strategy based on collaboration mechanism
Haiyan Lan (Harbin Engineering University)
and Shangyuan Wu (Harbin Engineering University)
Day 2 – August 15th, 2020 (Saturday) – Meeting Room 2 & Tencent Meeting ID: 496 675 279
Time:13:00-15:30 CST, 01:00-03:30 EDT
• Talks——R3: Edge Computing/Fog Computing
1.New Method of Traffic Flow Forecasting Based on QPSO Strategy for Internet of Vehicles
De-gan Zhang (Tianjin University of
Technology), Jing-yu Du (Tianjin University of Technology), Ting Zhang (Tianjin University of
Technology) and Hong-rui Fan (Tianjin University of Technology)
2.Sharing Economy: Implementing Decentralized Privacy-Preserving Parking System
Nejc Rožman (University of Ljubljana), Marko
Corn (University of Ljubljana) and Janez Diaci (University of Ljubljana)
3.IoT Enabled Smart Security Framework for 3D Printed Smart Home
Zhihan Xu (University of Electronic Science
and Technology of China), Shuja Ansari (University of Glasgow), Amir M. Abdulghani (University
of Glasgow, Sultan Qaboos University), Muhammad Ali Imran (University of Glasgow) and Qammer H.
Abbasi (University of Glasgow)
4.RFBBR: A Rtt Faireness Awared Algorithm Based on BBR
Weifeng Sun (Dalian University of
Technology), Minghan Jia (Dalian University of Technology), Guanghao Zhang (Dalian University of
Technology) and Zun Wang (Dalian University of Technology)
5.Dynamic and Accurate Force Feedback for Electromagnetic Haptic Display
Xiaosa Li (Wuhan University), Zhiyong Yuan
(Wuhan University), Jianhui Zhao (Wuhan University) and Xiangyun Liao (Chinese Academy of
Sciences)
6.Theoretical Modelling of Smart Meter Privacy Protection with Multi-meter Energy Routing
Cankut Ergen (Ozyegin University) and Burhan
Gulbahar (Ozyegin University)
Time:15:30-15:35 CST, 03:30-03:35 EDT
• Break
Time:15:35-17:45 CST, 03:35-05:45 EDT
• Talks——R4: Smart Cities, Intelligent Transportation and Internet of Vehicles
1.Analysis on Caching Strategy for Device-to-Device Communication with Multiple Helpers
Hui Song (South China Normal University),
Qunying Wu (South China Normal University), Zhikai Liu (South China Normal University), Feng Ke
(South China University of Technology), Daru Pan (South China Normal University) and Xian Zhou
(South China Normal University)
2.A Hybrid Approach for Intrusive Appliance Load Monitoring in Smart Home
Vanh Khuyen Nguyen (Macquarie University),
Minh-Hieu Phan (University of Wollongong), Wei Emma Zhang (University of Adelaide), Quan Z.
Sheng (Macquarie University) and Trung Duc Vo (CleverPal Pty Ltd)
3.A New Link Prediction in Directed Networks Based on Attributes Fusion
Zhicheng Li (People's Liberation Army
Strategic Support Force Information Engineering University), Lixin Ji (People's Liberation Army
Strategic Support Force Information Engineering University), Shuxin Liu (People's Liberation
Army Strategic Support Force Information Engineering University) and Jinsong Li (People's
Liberation Army Strategic Support Force Information Engineering University).
4.Scatter Balance based Semi-supervised Dimensional Reduction
Rui Yang (Dalian University of Technology,
Shenyang Normal University), Xiangzhu Meng (Dalian University of Technology) and LinFeng (Dalian
University of Technology)
5.A Discover of Class and Image Level Variance Between Different Pruning Methods on Convolutional Neural Networks
Shihong Gao (University of Electronic
Science and Technology of China)
6.Link Prediction Based on Information Preference Connection for Directed Network
Xuelei Zhao (PLA Strategic Support Force
Information Engineering University), Xinsheng Ji (PLA Strategic Support Force Information
Engineering University, National Digital Switching System & Engineering Technology Research
Center), Shuxin Liu (PLA Strategic Support Force Information Engineering University, National
Digital Switching System & Engineering Technology Research Center) and Zanyuan He (National
Digital Switching System & Engineering Technology Research Center)
Day 2 – August 15th, 2020 (Saturday) – Hallway & Tencent Meeting ID: 226 135 419
Time:13:00-17:30 CST, 01:00-05:30 EDT
• Talks——Poster Session
1.A low power circuit for medical drip infusion monitoring system
Shaojun Jiang (Dalian University of
Technology) and Yilin He (Dalian University of Technology)
2.An Intelligent Topology Optimization Strategy Toward the Robust Onion-like Structure
Qianzhen Sun (Dalian University of
Technology), Tie Qiu (Tianjin University) and He Guo (Dalian University of Technology)
3.A Blockchain-Indexed Storage supporting Scalable Data Integrity in Supply Chain Traceability
Shi-Syun Kuo (Aletheia University) and
Wei-Tsung Su (Aletheia University)
4.A Correlation Analysis of Indoor and Outdoor Air Quality using IoT sensors
Jaewon Moon (Korea Electronics Technology
Institute), Seungwoo Keum (Korea Electronics Technology Institute) and Sung-Soon Park (Anyang
University and Gluesys Co. LTD)
5.Design and development of a 3D Printed IoT portable Pillbox for continuous medication adherence
Dimitrios Karagiannis (National Technical
University of Athens) and Konstantina S. Nikita (National Technical University of Athens)
6.An Automatic Key-update Mechanism for M2M Communication and IoT Security Enhancement
Wen-Chung Tsai (Chaoyang University of
Technology), Tzu-Hsuan Tsai (Chaoyang University of Technology), Guang-Hao Xiao (Chaoyang
University of Technology), Te-Jen Wang (Institute for Information Industry ), Yu-Ruei Lian
(Chaoyang University of Technology) and Song-Hao Huang (Chaoyang University of Technology)
7.Development of IoT Edge Hub for Wireless Sensor Networks based on Docker Container
Natapon Tansangworn (National Electronics
and Computer Technology Center)
Day 3 – August 16th, 2020 (Sunday) – Meeting Room 1 & Tencent Meeting ID: 721 979 504
Time:13:00-15:30 CST, 01:00-03:30 EDT
• Talks——R5: Artificial Intelligence, Machine learning and Evolutionary Computing
1.Efficient Privacy-Preserving Electronic Voting Scheme Based on Blockchain
Ze Xu (Communication Communication
University of China) and Sanxing Cao (Communication Communication University of China)
2.Intelligent Instruction-Based IoT Framework for Smart Home Applications using Speech Recognition
Yao Ge (University of Glasgow), Shuja Ansari
(University of Glasgow), Amir Abdulghani (University of Glasgow), Muhammad Ali Imran (University
of Glasgow) and Qammer H. Abbasi (University of Glasgow)
3.On Threat Analysis of IoT-Based Systems: A Survey
Wenbing Zhao (Cleveland State University),
Shunkun Yang (Beihang University) and Xiong Luo (University of Science and Technology Beijing)
4.A Blockchain-based Approach for Assessing Compliance with SLA-guaranteed IoT Services
Ali Alzubaidi (Newcastle University, Umm
Al-Qura University), Karan Mitra (Luleå University of Technology, Pankesh Patel (Pandit
Deendayal Petroleum University) and Ellis Solaiman (Newcastle University)
5.TFBO: A Trusted Framework based on Blockchain for Outsourcing Data Entry
Fengqi Li (Key Lab for Ubiquitous Network
and Service Software of Liaoning Province, Dalian University of Technology), Chunli Shang
(Dalian University of Technology), Lupeng Zhang (Dalian University of Technology) and Jing Liu
(Dalian University of Technology)
6.Shortest Path Based Trained Indoor Smart Jacket Navigation System for Visually Impaired Person
Munmun Biswas (BGC Trust University
Bangladesh), Tanni Dhoom (Premier University), Refat Khan Pathan (BGC Trust University
Bangladesh) and Monisha Sen Chaiti (BGC Trust University Bangladesh)
7.Compact Fault Dictionaries for Efficient Sensor Fault Diagnosis in IoT-enabled CPSs
Stavros A. Viktoros (University of Cyprus),
Maria K. Michael (University of Cyprus) and Marios M. Polycarpou (University of Cyprus)
Time:15:30-15:35 CST, 03:30-03:35 EDT
• Break
Time:15:35-17:45 CST, 03:35-05:45 EDT
• Talks——S2: Social Networks, Multimedia and Mobile Computing
1.Multisize plate detection algorithm based on improved Mask RCNN
Feiyang Song (Guangdong University of
Technology), Liming Wu (Guangdong University of Technology), Gengzhe Zheng (Guangdong University
of Technology), Xinying He (Guangdong University of Technology), Guanchu Wu (Guangdong
University of Technology) and Yang Zhong (Guangdong University of Technology)
2.Hierarchical Formal Modeling of Internet of Things System Oriented to User Behavior
Lei Yu (Anhui University of Chinese
Medicine,Anhui Academy of Chinese Medicine), Yang Lu (Hefei University of Technology), Benhong
Zhang (Hefei University of Technology), Lei Shi (Hefei University of Technology), Fangliang
Huang (Anhui University of Chinese Medicine), Ya Li (Anhui University of Chinese Medicine) and
Yulian Shen (Anhui University of Chinese Medicine)
3.Learning IoT: Basic Experiments of Home Automation using ESP8266, Arduino and XBee
Annisa Sarah (Atma Jaya Catholic University
of Indonesia), Theresia Ghozali (Atma Jaya Catholic University of Indonesia), Geraldo Giano
(Atma Jaya Catholic University of Indonesia), Melisa Mulyadi (Atma Jaya Catholic University of
Indonesia), Sandra Octaviani (Atma Jaya Catholic University of Indonesia) and Alfin
Hikmaturokhman (Institut Teknologi Telkom Purwokerto)
4.The DevOps Reference Architecture Evaluation - A Design Science Research Case Study
Georges Bou Ghantous (University of
Technology Sydney) and Asif Gill (University of Technology Sydney)
5.Illegal Constructions Detection in Remote Sensing Images based on Multi-scale Semantic Segmentation
Chen Chen (Xidian University), Jiaxuan Deng
(Xidian University) and Ning Lv (Xidian University)
6.Wireless Signal Based Elderly Fall Detection Using XGboost Algorithm
Juan Wen (Nanchang Hangkong University),
Zhiyong Yang (Nanchang Hangkong University) and Lei Jin (Nanchang Hangkong University)
Day 3 – August 16th, 2020 (Sunday) – Meeting Room 2 & Tencent Meeting ID: 971 483 822
Time:13:00-15:30 CST, 01:00-03:30 EDT
• Talks——S1: Blockchain and Emerging Research or Technologies
1.Characteristic Perception of Mixed Pulley Sound Signal Based on Clustering Hidden Markov Model
Gengzhe Zheng (Guangdong University of
Technology), Liming Wu (Guangdong University of Technology), Feiyang Song (Guangdong University
of Technology), Xinying He (Guangdong University of Technology), Gengxuan Lin (Guangdong
University of Technology) and Danfeng Jiang (Guangdong University of Technology)
2.Supply Chain Financial Model Innovation Based on Block-chain Drive and Construction of Cloud Computing Credit System
Yifei Yao (JimeiUniversity), Liangyong Chu
(JimeiUniversity), Linyun Shan (JimeiUniversity) and Qihui Lei (JimeiUniversity)
3.An In-class Teaching Comprehensive Evaluation Model Based on Statistical Modelling and Ensemble Learning
Ludi Bai (Beijing Normal University), Zehui
Yu (Beijing Normal University), Shifeng Zhang (Hangzhou Hikvision Digital Technology Co., Ltd.),
Kangying Hu (Hangzhou Hikvision Digital Technology Co., Ltd.), Zhan Chen (Hangzhou Hikvision
Digital Technology Co., Ltd.) and Junqi Guo (Beijing Normal University)
4.In-depth Real-World Evaluation of NB-IoT Module Energy Consumption
Milan Lukic (University of Novi Sad), Srdjan
Sobot (University of Novi Sad), Ivan Mezei, (University of Novi Sad), Dejan Vukobratovic
(University of Novi Sad) and Dragan Danilovic (VIP Mobile)
5.NOMA-based Slotted p-Persistent CSMA with Multipacket Reception from Power Domain
Tingyu Qi (Tsinghua University, Beijing
National Research Center for Information Science and Technology (BNRist)) and Youzheng Wang
(Tsinghua University, Beijing National Research Center for Information Science and Technology
(BNRist))
6.IoT Based Smart Farming: Are the LPWAN Technologies Suitable for Remote Communication?
Nahina Islam (Central Queensland
University), Biplob Ray (Central Queensland University) and Faezeh Pasandideh (Islamic Azad
University)
Time:15:30-15:35 CST, 03:30-03:35 EDT
• Break
Time:15:35-17:45 CST, 03:35-05:45 EDT
• Talks——S3: Control and Decision Making for Smart IoT or CPS
1.XuperChain: A blockchain system that supports smart contracts parallelization
Xiao Wei (Baidu Blockchain Lab), Sun Junyi
(Baidu Blockchain Lab), Zheng Qi (Baidu Blockchain Lab) and Chen Fu (Central University of
Finance and Economics)
2.Mediating Data Trustworthiness by Using Trusted Hardware between IoT Devices and Blockchain
Batnyam Enkhtaivan (NEC Corporation) and
Akiko Inoue (NEC Corporation)
3.Research of Power Energy Management Control Strategy with IOT in NZEB
Qingguang Yu (Tsinghua University), Zhicheng
Jiang (Tsinghua University), Yuming Liu (Tsinghua University) and Gaoxiang Long (Tsinghua
University)
4.Analysis of Resource Allocation Overheads in Vehicle Ad Hoc Network Considering CSI
Min Ao (Beijing University of Posts and
Telecommunications) and Xin Zhang (Beijing University of Posts and Telecommunications)
5.Research on Artificial Fish Swarm Clustering Algorithm in Urban Internet of Vehicles
Fengxin Cheng (Southwest Minzu University)
and Caixing Shao (Southwest Minzu University, University of Electronic Science and Technology of
China)
6.Fork Probability Analysis of PoUW Consensus Mechanism
Zhijie Ma (Macau University of Science and
Technology, Institute of Microelectronics of the Chinese Academy of Science, Jiangsu Research
and Development Center for Internet of Things), Qinglin Zhao (Macau University of Science and
Technology), Jianwen Yuan (Macau University of Science and Technology), Xiaobo Zhou (Tianjin
University), and Li Feng (Macau University of Science and Technology)
7.A Cyber-Physical System Approach for Predictive Maintenance
Koonlachat Meesublak (National Electronics
and Computer Technology Center) and Tosapol Klinsukont (National Electronics and Computer
Technology Center)
|